#how to check powershell version
Explore tagged Tumblr posts
Text
KIP'S BIG POST OF THINGS TO MAKE THE INTERNET & TECHNOLOGY SUCK A LITTLE LESS

Post last updated November 23, 2024. Will continue to update!
Here are my favorite things to use to navigate technology my own way:
A refurbished iPod loaded with Rockbox OS (Rockbox is free, iPods range in price. I linked the site I got mine from. Note that iPods get finicky about syncing and the kind of cord it has— it may still charge but might not recognize the device to sync. Getting an original Apple cord sometimes helps). Rockbox has ports for other MP3 players as well.
This Windows debloater program (there are viable alternatives out there, this one works for me). It has a powershell script that give you a little UI and buttons to press, which I appreciate, as I'm still a bit shy with tech.
Firefox with the following extensions: - Consent-O-Matic (set your responses to ALL privacy/cookie pop-ups in the extension, and it will answer all pop-ups for you. I can see reasons to not use it, but I appreciate it) - Facebook Container ("contains" Meta on Facebook and Instagram pages to keep it from tracking you or getting third party cookies, since Meta is fairly egregious about it) - Redirect Amp to HTML (AMP is designed for mobile phones, this forces pages to go to their HTML version) - A WebP/AVIF image converter - uBlock Origin and uBlacklist, with the AI blacklist loaded in to kill any generative AI results from appearing in search engines or anywhere.
Handbrake for ripping DVDs— I haven’t used this in awhile as I haven’t been making video edits. I used this back when I had a Mac OS
VLC Media Player (ol’ reliable)
Unsplash & Pexels for free-to-use images
A password manager (these often are paid. I use Dashlane. There are many options, feel free to search around and ask for recs!). There is a lot that goes into cybersecurity— find the option you feel is best for you.
Things I suggest:
Understanding Royalty Free and the Creative Commons licenses
Familiarity with boolean operators for searching
Investing in a backup drive and external drive
A few good USBs, including one that has a backup of your OS on it
Adapter cables
Avoiding Fandom “wikias” (as in the brand “Fandom”) and supporting other, fan-run or supported wikis. Consider contributing if its something you find yourself passionate or joyful about.
Finding Forums for the things you like, or creating your own*
Create an email specifically for ads/shopping— use it to receive all promotional emails to keep your inbox clean. Upkeep it.
Stop putting so much of your personal information online— be willing to separate your personal online identity from your “online identity”. You don’t owe people your name, location, pronouns, diagnoses, or any of that. It’s your choice, but be discerning in what you give and why. I recommend avoiding providing your phone number to sites as much as possible.
Be intentional
Ask questions
Talk to people
Remember that you can lurk all you want
Things that are fun to check out:
BBSes-- here's a portal to access them.
Neocities
*Forums-- find some to join, or maybe host your own? The system I was most familiar with was vbulletin.
MMM.page
Things that have worked well for me but might work for you, YMMV:
Limit your app usage time on your smartphone if you’re prone to going back to them— this is a tangible way to “practice mindfulness”, a term I find frustratingly vague ansjdbdj
Things I’m looking into:
The “Pi Hole”— a raspberry pi set up to block all ads on a specific internet connection
VPNs-- this is one that was recommended to me.
How to use computers (I mean it): Resources on how to understand your machine and what you’re doing, even if your skill and knowledge level is currently 0:
This section I'll come back an add to. I know that messing with computers can be intimidating, especially if you feel out of your depth. HTML and regedits and especially things like dualbooting or linux feel impossible. So I want to put things here that explain exactly how the internet and your computer functions, and how you can learn and work with that. Yippee!
851 notes
·
View notes
Text

Tools of the Trade for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Cybersecurity professionals use a lot of different tools to get the job done. There are plenty of fancy and expensive tools that enterprise security teams use, but luckily there are also lots of brilliant people writing free and open-source software. In this post, I'm going to list some popular free tools that you can download right now to practice and learn with.
In my opinion, one of the most important tools you can learn how to use is a virtual machine. If you're not already familiar with Linux, this is a great way to learn. VMs are helpful for separating all your security tools from your everyday OS, isolating potentially malicious files, and just generally experimenting. You'll need to use something like VirtualBox or VMWare Workstation (Workstation Pro is now free for personal use, but they make you jump through hoops to download it).
Below is a list of some popular cybersecurity-focused Linux distributions that come with lots of tools pre-installed:
Kali is a popular distro that comes loaded with tools for penetration testing
REMnux is a distro built for malware analysis
honorable mention for FLARE-VM, which is not a VM on its own, but a set of scripts for setting up a malware analysis workstation & installing tools on a Windows VM.
SANS maintains several different distros that are used in their courses. You'll need to create an account to download them, but they're all free:
Slingshot is built for penetration testing
SIFT Workstation is a distro that comes with lots of tools for digital forensics
These distros can be kind of overwhelming if you don't know how to use most of the pre-installed software yet, so just starting with a regular Linux distribution and installing tools as you want to learn them is another good choice for learning.
Free Software
Wireshark: sniff packets and explore network protocols
Ghidra and the free version of IDA Pro are the top picks for reverse engineering
for digital forensics, check out Eric Zimmerman's tools - there are many different ones for exploring & analyzing different forensic artifacts
pwntools is a super useful Python library for solving binary exploitation CTF challenges
CyberChef is a tool that makes it easy to manipulate data - encryption & decryption, encoding & decoding, formatting, conversions… CyberChef gives you a lot to work with (and there's a web version - no installation required!).
Burp Suite is a handy tool for web security testing that has a free community edition
Metasploit is a popular penetration testing framework, check out Metasploitable if you want a target to practice with
SANS also has a list of free tools that's worth checking out.
Programming Languages
Knowing how to write code isn't a hard requirement for learning cybersecurity, but it's incredibly useful. Any programming language will do, especially since learning one will make it easy to pick up others, but these are some common ones that security folks use:
Python is quick to write, easy to learn, and since it's so popular, there are lots of helpful libraries out there.
PowerShell is useful for automating things in the Windows world. It's built on .NET, so you can practically dip into writing C# if you need a bit more power.
Go is a relatively new language, but it's popular and there are some security tools written in it.
Rust is another new-ish language that's designed for memory safety and it has a wonderful community. There's a bit of a steep learning curve, but learning Rust makes you understand how memory bugs work and I think that's neat.
If you want to get into reverse engineering or malware analysis, you'll want to have a good grasp of C and C++.
Other Tools for Cybersecurity
There are lots of things you'll need that aren't specific to cybersecurity, like:
a good system for taking notes, whether that's pen & paper or software-based. I recommend using something that lets you work in plain text or close to it.
general command line familiarity + basic knowledge of CLI text editors (nano is great, but what if you have to work with a system that only has vi?)
familiarity with git and docker will be helpful
There are countless scripts and programs out there, but the most important thing is understanding what your tools do and how they work. There is no magic "hack this system" or "solve this forensics case" button. Tools are great for speeding up the process, but you have to know what the process is. Definitely take some time to learn how to use them, but don't base your entire understanding of security on code that someone else wrote. That's how you end up as a "script kiddie", and your skills and knowledge will be limited.
Feel free to send me an ask if you have questions about any specific tool or something you found that I haven't listed. I have approximate knowledge of many things, and if I don't have an answer I can at least help point you in the right direction.
#studyblrmasterpostjam#studyblr#masterpost#cybersecurity#late post bc I was busy yesterday oops lol#also this post is nearly a thousand words#apparently I am incapable of being succinct lmao
22 notes
·
View notes
Note
hi im good with computers some of the time! what exactly is the problem and what have you tried? -red
oh hey red! good to hear from you!
so, it's kind of a lot to explain. we have an asus rog strix laptop (running win10) that had a broken monitor at one point. after sending it to asus and getting it repaired and sent back, we werent able to sign in to our microsoft account in the computer settings. because of that, we can't open the microsoft store or use any apps that come with the laptop (i.e. calendar, alarms, couldn't even use the armoury crate app that asus gives out). we also couldn't run any installer unless we go into the properties and unblock it first.
after a while, we found that running setup commands thru powershell/cmd prompt will mostly work. so, yesterday, we were trying to install some microsoft app via msixbundle in powershell (using "Add-AppxPackage") but it spat back out this error at us:
Windows cannot install package [REDACTED] because this package depends on a framework that could not be found. Provide the framework "Microsoft.UI.Xaml.2.8" published by "CN=Microsoft Corporation, O=Microsoft Corporation, L=Redmond, S=Washington, C=US", with neutral or x64 processor architecture and minimum version 8.2212.15002.0, along with this package to install. The frameworks with name "Microsoft.UI.Xaml.2.8" currently installed are: {}
now i know that doesnt mean that we dont have any frameworks, but i like to be dramatic (and i dont know what specifically are frameworks or not so idk how to check that)
anyway that's basically it. we've never successfully installed any windows/microsoft/etc. app to our computer (word, excel, etc) and in order to install ANY app we have to manually unblock it or else it freezes up the entire application we try to run it in (i.e. file explorer, firefox's downloads page, the fucking desktop, etc.). we have occasional success with using run commands, but it doesn't work all of the time (will still freeze cmd prompt) and that only works for third party stuff really.
#✨#Anonymous#not art#(( basil 🧲 any ))#sorry if its worded weird or doesnt make sense. im really frustrated by this lol#our partner made a reddit post about the installer freezing our computer thing a while ago but this is more of a microsoft issue than-#-an installer issue rn i think#but i feel that its all related to each other since it happened at the same time yk?
2 notes
·
View notes
Text

The one thing about cyber security that you should always be aware of is its ongoing state of evolution. Threats are constantly evolving; thus, your defensive strategy cannot become inert. This is not overly dramatic. Attacks occurred around every 39 seconds in 2023. Approximately 40% of all attacks are script-based, meaning that malevolent actors have unlimited access to resources. IT experts and managed service providers (MSPs) and rmm tools and PSA software suppliers must exercise caution. We have compiled a list of some of the biggest cybersecurity threats and vulnerabilities from recent history to assist. This is the impact of the shifting landscape on security-conscious individuals. What is cyber security? A catch-all word for reducing the risks of cyberattacks is cybersecurity. Organizations employ a range of procedures, technologies, and controls to practice adequate cyber security, including: Keep information, software, hardware, networks, and other assets safe from real-time unauthorized access and exploitation. Examine potential risks Practice emergency response and simulate hacking. reaction techniques Establish policies to encourage the safe use of information and technology. How do vulnerabilities and threats to computer security operate? Malicious actors can obtain unauthorized access to sensitive data through many means. Also Read: What is SHA256 Encryption: How it Works and Applications Existing weaknesses are often exploited in events. For example, hackers may leverage a widely recognized vulnerability to obtain backdoor access. Alternatively, they can uncover fresh vulnerabilities associated with your technology usage. In either case, these incidents frequently involve ransom demands, legal dangers, and bad public relations. Not every bad actor is a Hollywood hacker working for a hidden organization of cybercriminals. Anyone can cause a breach, even a contracting agency, from irate workers and roguish states to terrorists and corporate spittle. Strong safeguards should be put in place before that occurs! Here are a few of the most noteworthy threats that have emerged in the most recent headlines: Twitter Email Leak The Twitter data breach occurred only a few days after the year 2022 came to an end. In summary, the email addresses of more than 200 million Twitter users were exposed on underground hacking websites. The affected Twitter accounts surpassed 400 million. Hackers began gathering data in 2021 by taking advantage of a vulnerability in the Twitter API. Several hackers took use of this vulnerability back in 2021, which led to multiple ransomware attempts and leaks in 2022. One of the biggest data breaches in history is this one. Also Read: Guide to Check Which Powershell Version You are UsingGuide to Check Which Powershell Version You are Using The Royal Mail Hack The UK's Royal Mail was compromised by the Russian ransomware group LockBit in January 2023. The hackers demanded a ransom of £65 million to unlock the compromised data. The business requested that customers cease sending items overseas due to the severity of the event! This may seem like a success story in certain ways. Ultimately, Royal Mail declined to provide a ransom. Unfortunately, there were prolonged service outages and many of its employees had their data disclosed. This cybersecurity event demonstrates that averting a hack's worst-case scenario is a minor comfort. The worst-case scenario persists, and the erosion of public trust is a severe blow for national infrastructure-level companies such as the Royal Mail. The Reddit Hack The forum site Reddit disclosed in February 2023 that the user was a recent victim of spear phishing. Through a phishing attack targeted at employees, hackers were able to access internal Reddit data. In addition, the hackers desired ransom money. THE OUTCOME? Financial information was leaked along with the personal information of hundreds of current and former faculty members, staff members, and advertisers. Reddit's emergency response team was able to resolve the issue swiftly. However, this was an event that the business ought to have completely avoided. The phishing attack functioned by impersonating a page from the internal portal of the business. This tricked at least one worker into disclosing their access credentials—and all it takes is one! T-Mobile Data Breach: T-Mobile USA had two hacks. Late in 2022, T-Mobile disclosed that 37 million users' personal data had been accessed by a malevolent attacker. The most recent breach was found in March. Comparing the volume of stolen data to the previous breach, it was less. A total of 836 customers had their PINs, account information, and personal details compromised due to this cyber security threat. Information on personal bank accounts was not taken. Also Read: What is BSSID? The ChatGPT Payment Exposure The widely used ChatGPT Plus service experienced a major outage in March 2023. Even though the interruption was brief—about nine hours—it caused no appreciable harm. The payment information of more than one percent of subscribers was disclosed to other users. The communication histories of certain users also become accessible. While 1. 2 may not seem like a big number, it represents yet another instance of a lost user's trust. In this instance, OpenAI was unable to properly retrieve an open-source library, a huge mistake! When you are unable to secure your software supply chain, it does not look good. This event might hurt a tech company's competitiveness in an expanding industry like artificial intelligence. Also Read: How To Take Screenshots on Windows and Mac AT&T 3rd Party Data Breach In March 2023, a third-party data breach exposed 9 million customer records belonging to another titan in the telecom industry, AT&T. AT&T classified this threat as a supply chain assault involving data that was several years old and largely related to eligibility for device upgrades. Consequently, the telecom advised its clients to implement more robust password security protocols. VMware ESXi Ransomware In January of last year, a ransomware attack using an outdated vulnerability (CVE-2021-21974) affected about 3,200 unpatched VMware ESXi servers. Via CVE-2021-21974, hackers began a ransomware assault against VMware ESXi hypervisors. They were able to use this readily exploitable vulnerability to remotely exploit code without the need for previous authentication. France was the most affected nation, with the United States, Germany, and Canada following suit. Concerning CrowdStrike, the issue is becoming more serious. "A growing number of threat actors are realizing that an environment rich in targets is created by inadequate network segmentation of ESXi intrusions, a lack of security tools, and ITW vulnerabilities for ESXi." How can MSPs get ready for threats and vulnerabilities related to cyber security? Use these four practical suggestions to enhance your cybersecurity strategy and mitigate threats and vulnerabilities: Make data backups a regular part of your life. Adhere to the 3-2-1 backup policy. Store three duplicates of your information on two or more media types. One copy will be stored on your primary system. The other two ought to be locally and cloud-based encrypted backups. Reduce your exposure to the least amount possible. Installing firewalls or antivirus software alone won't cut it. Additionally, you must keep them updated. Also Read: What is a VLAN (Virtual LAN)? Author Bio Fazal Hussain is a digital marketer working in the field since 2015. He has worked in different niches of digital marketing, be it SEO, social media marketing, email marketing, PPC, or content marketing. He loves writing about industry trends in technology and entrepreneurship, evaluating them from the different perspectives of industry leaders in the niches. In his leisure time, he loves to hang out with friends, watch movies, and explore new places. Read the full article
0 notes
Text
Everything You Need to Know About iManage: A Comprehensive Guide for Law Firms
In the ever-evolving world of legal practice, managing documents and emails efficiently is crucial. iManage, a leading provider of document and email management systems, plays a pivotal role in the smooth operation of law firms, corporate legal departments, and other professional services. This blog will explore various aspects of iManage, including iManage Outlook, iManage WorkSite Manual, iManage PowerShell, iManage News, iManage Records, and its importance for law firms.
1. iManage Outlook: Streamlining Email and Document Management
iManage Outlook is a robust integration that connects Microsoft Outlook with iManage, offering a seamless experience for managing email correspondence and documents. With iManage Outlook, legal professionals can easily file emails into the appropriate client or matter, ensuring that important information is organized and easily accessible.
The integration also enables users to save emails directly from Outlook to iManage, tagging them for future retrieval. This integration enhances efficiency by keeping emails and documents connected, thus reducing the time spent searching for critical information.
For law firms looking to optimize their workflow, iManage Outlook is an indispensable tool. Learn more about integrating iManage with your email system at MacroAgility's iManage Email and Document Work 10 and Share.
2. iManage WorkSite Manual: Empowering Teams with Centralized Document Management
iManage WorkSite is the foundation for document and email management, offering a secure and centralized system for storing, organizing, and retrieving files. The iManage WorkSite manual is a comprehensive guide that helps users understand how to navigate and maximize the capabilities of WorkSite.
With WorkSite, legal teams can easily track revisions, manage versioning, and collaborate on files without worrying about data loss. The platform’s user-friendly interface makes it easy for team members to access the information they need while maintaining the highest standards of security and compliance. For law firms, this is an essential tool to maintain a secure and organized digital ecosystem.
3. iManage PowerShell: Automating Tasks for Efficiency
iManage PowerShell is a scripting tool designed to automate routine tasks and streamline operations within iManage. This powerful tool is used by IT professionals and administrators to simplify processes such as document management, user provisioning, and security configurations.
By using iManage PowerShell, organizations can reduce manual errors, improve workflow efficiency, and ensure that their iManage environment is configured to meet their specific needs. Automation helps free up resources, allowing legal professionals to focus on higher-value tasks rather than mundane, repetitive activities.
For more information on iManage PowerShell, check out additional resources like MacroAgility’s Lotus to Outlook, where you can discover how automation can be seamlessly integrated into your practice.
4. iManage News: Staying Updated on Latest Developments
Keeping up with the latest trends and updates is crucial in the legal tech world. iManage regularly releases news updates that include new features, product enhancements, and case studies demonstrating how their systems improve efficiency and security.
Staying updated with iManage News ensures that law firms can take advantage of the latest advancements in document management technology. These updates also help businesses stay compliant with regulatory requirements, keeping their systems up-to-date with the latest legal and industry standards.
For the most recent iManage news and updates, visit MacroAgility’s News and Events to learn about the latest happenings and innovations in the industry.
5. iManage Records: Ensuring Compliance and Security
For law firms, document security and compliance are non-negotiable. iManage Records provides a comprehensive solution for managing, securing, and archiving important legal documents and records. This module allows firms to enforce retention policies, automate compliance checks, and protect sensitive client information.
The integration of iManage Records ensures that legal firms adhere to strict regulatory requirements while maintaining efficient and secure management of critical documents. This solution helps minimize the risk of data breaches and ensures that documents are disposed of in accordance with legal standards when their retention period expires.
6. iManage for Law Firms: A Game-Changer in Legal Document Management
For law firms, managing client files, emails, and documents is a challenging task. iManage provides the perfect solution by offering an intuitive and secure platform for organizing, searching, and sharing documents. Whether you are dealing with legal briefs, case files, or corporate agreements, iManage’s user-friendly interface makes it easy to store and retrieve critical documents with just a few clicks.
Law firms, in particular, benefit from iManage’s advanced security features, version control, and seamless integration with other tools like Microsoft Office. With iManage, law firms can enhance collaboration, boost productivity, and reduce the risks associated with document mismanagement.
Why Choose MacroAgility for iManage Solutions?
At MacroAgility, we specialize in providing businesses with solutions tailored to meet their specific document management needs. Whether you are transitioning from Lotus Notes to Outlook or implementing iManage for the first time, our expert team ensures a smooth and hassle-free experience.
We also offer services like data migration, training, and ongoing support, ensuring that your iManage environment remains efficient and up-to-date. Explore our services to learn more about how we can help your firm optimize document management and improve overall productivity.
Conclusion
iManage is a crucial tool for modern law firms looking to streamline their document management processes, enhance collaboration, and ensure compliance with industry regulations. From the powerfulimanage worksite manual integration to the secure iManage Records solution, this platform provides everything a law firm needs to stay organized and efficient.
For more information on how iManage can transform your firm, reach out to MacroAgility. Our team of experts is ready to assist you in implementing the best solutions tailored to your needs.
Stay updated with the latest developments in the legal tech space by visiting MacroAgility’s News and Events.
#imanage outlook#imanage worksite manual#imanage powershell#imanage news#imanage records#imanage law firms
0 notes
Text
How to Check Motherboard Model in Windows 10 – Easy & Quick Methods

When troubleshooting hardware issues, upgrading components, or checking compatibility, knowing your motherboard model is crucial. If you’re using Windows 10 and wondering, “How to check motherboard model in Windows 10?”, you’ve come to the right place.
In this guide, we’ll walk you through multiple methods to find your motherboard model without opening your PC. These methods work on Windows 7, Windows 10, and newer versions. Let’s dive in!
Why Do You Need to Check Your Motherboard Model?
Before we explore the methods, let’s understand why identifying your motherboard model is important:
✔ Upgrading Hardware – Check compatibility for CPU, RAM, or GPU upgrades. ✔ Driver Updates – Ensure you install the correct motherboard drivers. ✔ BIOS Updates – Find the right BIOS firmware for stability and performance. ✔ Troubleshooting Issues – Diagnose and fix hardware-related problems. ✔ Warranty and Support – Contact your manufacturer for warranty-related queries.
Now, let’s explore different methods to check the motherboard model in Windows 10.
1. How to Check Motherboard Model in Windows 10 Using Command Prompt
The easiest way to check your motherboard model in Windows 10 is by using Command Prompt. Follow these steps:
1️⃣ Press Win + R, type cmd, and hit Enter to open the Command Prompt. 2️⃣ Type the following command and press Enter:wmic baseboard get product,manufacturer,version,serialnumber
3️⃣ The manufacturer, model, version, and serial number of your motherboard will be displayed.
Example Output:Manufacturer Product Version SerialNumber ASUS PRIME B450M-A Rev 1.02 XXXXXXXXXXX
This method is quick and doesn’t require any third-party software.
2. How to Find Motherboard Model in Windows 10 Using System Information
Windows 10 has a built-in tool called System Information that can help you check your motherboard model.
1️⃣ Press Win + R, type msinfo32, and hit Enter. 2️⃣ In the System Summary, look for BaseBoard Manufacturer and BaseBoard Product. 3️⃣ This will display your motherboard’s brand and model.
🔹 If the motherboard model is missing, try other methods in this guide.
3. How to Check My Motherboard Model Using Windows PowerShell
PowerShell is another built-in Windows tool that helps retrieve system details.
1️⃣ Right-click on the Start menu and select Windows PowerShell (Admin). 2️⃣ Enter the following command:Get-WmiObject Win32_BaseBoard | Format-List Product,Manufacturer,SerialNumber,Version
3️⃣ Press Enter to get your motherboard details.
4. How to Check Motherboard Model in Windows 10 Using Third-Party Software
If you want a more detailed report of your motherboard, try using third-party tools like CPU-Z or Speccy.
Using CPU-Z
1️⃣ Download and install CPU-Z. 2️⃣ Open the program and go to the Mainboard tab. 3️⃣ Here, you’ll see the motherboard manufacturer, model, chipset, and BIOS version.
Using Speccy
1️⃣ Download Speccy and install it. 2️⃣ Open Speccy and navigate to Motherboard in the left menu. 3️⃣ You’ll find detailed information about your motherboard, including manufacturer, model, and version.
These tools provide more in-depth details about your motherboard and other hardware components.
5. How to Check Motherboard Model in Windows 7 & Older Versions
If you're running Windows 7, the steps are similar to Windows 10:
✔ Command Prompt – Use wmic baseboard get product,manufacturer,version,serialnumber. ✔ System Information – Open msinfo32 and check BaseBoard details. ✔ Third-Party Tools – CPU-Z and Speccy work on Windows 7 and Windows 10.
Windows 7 users may experience limitations in System Information, but the Command Prompt method works perfectly.
6. How to Check Motherboard Model If Windows Won’t Boot?
If your system isn’t booting, you can still find your motherboard model:
1️⃣ Check Your Motherboard – Look for the model name printed on the motherboard itself. 2️⃣ BIOS/UEFI Settings – Restart your PC and press F2, F10, or DEL to enter BIOS. The model is often displayed on the main screen. 3️⃣ Check the Packaging or Invoice – If you bought a prebuilt PC, the motherboard model is listed in the invoice or manual.
Final Thoughts
Knowing how to check your motherboard model in Windows 10 is essential for upgrades, troubleshooting, and driver updates. The Command Prompt, System Information, and PowerShell methods are the easiest ways to find motherboard details without additional software. If you need detailed hardware insights, third-party tools like CPU-Z and Speccy are excellent options.
Still have questions about your motherboard model? Visit Dell Laptop Service Center in Mumbai for expert guidance on hardware upgrades, repairs, and diagnostics.
📌 Need help? Contact our experts today! ✅
#MotherboardCheck#Windows10Tips#PCUpgrade#TechGuide#LaptopRepair#MotherboardModel#Windows7Help#HardwareCheck#BIOSUpdate#PCDiagnostics#DellService#TechSupport#ComputerRepair#SystemInfo#CheckMotherboard#PCMaintenance#LaptopUpgrades#TechSolutions#ComputerTips#WindowsHelp
0 notes
Text
A Quick Guide to Check if .NET is Already Installed on Your System
If you’re about to start a .NET project or install software that relies on the .NET Framework, it’s important to know whether .NET is already installed on your system. Thankfully, checking for .NET installations is straightforward and doesn’t require advanced technical skills. Here’s how you can easily verify if .NET is installed on your system.
Methods to Check for .NET Installation: -
1. Using Command Prompt (Windows)
You can quickly check if .NET is installed by running a simple command in the Command Prompt.
Steps:
Open Command Prompt by searching for it in the Start Menu.
Enter the following command:

This command will display the versions of .NET Framework installed on your system. Look for the version number under the subkeys like v4.0, v3.5, etc.
2. Using PowerShell (Windows)
PowerShell is another great option to check for .NET installations. The following command works for .NET Framework and .NET Core.
Open PowerShell by searching for it in the Start Menu. This will show all installed versions of .NET SDKs and runtimes.
3. Checking via Control Panel (Windows)
You can also check for .NET installations using the Control Panel.
Steps:
Go to Control Panel > Programs > Programs and Features.
Scroll through the list of installed programs and look for entries that start with “Microsoft .NET Framework” or “.NET Core.”
This method gives you a clear, visual confirmation of .NET installations.
How Memetic Solutions Can Help
At Memetic Solutions, we specialize in building reliable, scalable applications tailored to your business needs. Whether you’re looking to update your current environment, troubleshoot installation issues, or develop cutting-edge software using the .NET framework, our team of experts is here to assist you.
Feel free to visit our website or contact us anytime for more information on our .NET development services.
#DotNet#DotNetFramework#DotNetCore#TechSupport#WebDevelopment#MemeticSolutions#SoftwareDevelopment#NetDevelopment#Windows#Microsoft
0 notes
Text
Enterprise Automation Expert Track: Unlocking Efficiency and Scalability
In today's fast-paced business environment, the demand for automation has skyrocketed as organizations strive to increase efficiency, reduce operational costs, and maintain a competitive edge. For professionals looking to stay ahead of the curve, mastering enterprise automation is essential. The Enterprise Automation Expert Track is designed to equip you with the skills and knowledge needed to lead automation initiatives within your organization.
Why Enterprise Automation?
Enterprise automation involves the use of technology to perform repetitive tasks, streamline processes, and enhance overall productivity. It spans across various domains including IT operations, business processes, and even customer service. By automating routine tasks, companies can focus on innovation, strategic planning, and delivering value to customers.
Key benefits of enterprise automation include:
Increased Efficiency: Automation reduces the time and effort required to complete tasks, leading to faster execution and improved efficiency.
Cost Savings: By automating manual processes, organizations can significantly cut down on labor costs and minimize errors.
Scalability: Automated systems can easily scale to accommodate business growth, allowing organizations to expand without the need for proportional increases in resources.
Improved Accuracy: Automation eliminates the risk of human error, ensuring consistent and accurate results.
What You’ll Learn in the Enterprise Automation Expert Track
This track is designed for IT professionals, system administrators, DevOps engineers, and anyone looking to specialize in enterprise automation. Here’s a glimpse of what you’ll learn:
Introduction to Automation Tools:
Gain a solid understanding of the most popular automation tools in the industry, including Ansible, Puppet, Chef, and Jenkins.
Learn how to choose the right tool for your organization's specific needs.
Advanced Scripting and Orchestration:
Master scripting languages like Python and PowerShell for automating tasks.
Explore orchestration techniques to manage complex workflows across multiple systems.
Infrastructure as Code (IaC):
Learn the principles of Infrastructure as Code and how to apply them using tools like Terraform.
Understand the importance of version control and automation in managing infrastructure at scale.
Continuous Integration/Continuous Deployment (CI/CD):
Dive into the world of CI/CD pipelines and learn how to automate the entire software delivery process.
Explore best practices for integrating testing and deployment into your CI/CD pipelines.
Security Automation:
Understand the critical role of automation in enhancing security.
Learn how to implement automated security measures, including vulnerability scanning and compliance checks.
Monitoring and Analytics:
Discover how to set up automated monitoring systems to track performance, identify issues, and optimize operations.
Explore the use of analytics in automation to drive data-driven decision-making.
Why Choose the Enterprise Automation Expert Track?
Hands-on Learning: The track offers practical, hands-on labs and real-world scenarios to help you apply what you've learned.
Expert Instructors: Learn from industry experts with extensive experience in enterprise automation.
Certification: Upon completion, earn a certification that validates your expertise and enhances your career prospects.
Conclusion
The Enterprise Automation Expert Track is more than just a learning path—it's your gateway to becoming a leader in automation. As businesses continue to embrace digital transformation, the demand for automation experts will only grow. By enrolling in this track, you'll gain the skills and confidence to drive automation initiatives and lead your organization into the future.
Ready to take the next step in your career? Enroll in the Enterprise Automation Expert Track today and start your journey towards becoming an automation leader!
For more details click www.hawkstack.com
#redhatcourses#docker#information technology#containerorchestration#container#kubernetes#containersecurity#linux#dockerswarm#aws#hawkstack#hawkstacktechnologies
0 notes
Text
How to Know Which Version of Windows You Have: A Complete Guide

Have you ever wondered which version of Windows your computer is running? Whether you're a tech newbie or a seasoned user, knowing your Windows version is crucial for compatibility with software, drivers, and updates. This guide will walk you through the simplest methods to find out your Windows version, along with some extra tips and tricks to enhance your knowledge. Let’s dive in!
Understanding the Importance of Knowing Your Windows Version
Knowing your Windows version is essential for several reasons:
Software Compatibility: Ensures that applications and programs run smoothly.
Security Updates: Keeps your system protected with the latest security patches.
Troubleshooting: Helps resolve system issues more efficiently.
Methods to Determine Your Windows Version
Here are some easy ways to check your Windows version:
Method 1: Using System Settings
Open Settings:
Press Windows + I to open the Settings menu.
Navigate to System:
Click on "System" and then "About".
Check Windows Specifications:
Here, you’ll find your Windows edition and version.
Method 2: Using the Run Dialog
Open the Run Dialog:
Press Windows + R.
Type winver:
In the Run box, type winver and press Enter.
View the Information:
A window will pop up displaying your Windows version and build number.
Method 3: Using Command Prompt
Open Command Prompt:
Press Windows + X and select "Command Prompt" or "Windows PowerShell".
Type the Command:
Enter systeminfo and press Enter.
Check Windows Version:
Scroll through the information to find the "OS Name" and "Version".
Additional Methods
Using Control Panel: Navigate to Control Panel > System and Security > System to view your Windows version.
Windows Logo: On older versions like Windows 7, the Start menu logo gives a clue about the version.
Understanding Windows Version Numbers and Build Numbers
Microsoft frequently updates Windows, releasing major versions and build numbers. Here’s a quick rundown:
Windows 10: Known for its frequent updates, e.g., Version 20H2, 21H1.
Windows 11: The latest version with an updated interface and new features.
Addressing Common Questions
Q: Can I upgrade my Windows version for free? A: Yes, Microsoft often offers free upgrades from older versions to the latest one, like from Windows 10 to Windows 11.
Q: How can I find out if my Windows version is genuine? A: Check your activation status by going to Settings > Update & Security > Activation.
Tips to Keep Your Windows System Up-to-Date
Enable Automatic Updates: Ensure your system receives the latest updates.
Regularly Check for Updates: Manually check for updates by going to Settings > Update & Security > Windows Update.
Use Trusted Sources: Download updates and software from official sources to avoid malware.
External Links to Authoritative Sources
Microsoft Support: Find your Windows version - Official guide from Microsoft.
How-To Geek: How to Determine Which Version of Windows You Are Running - A reliable tech site with additional tips.
PCWorld: How to Check Your Windows Version - Another trusted tech resource.
By following this comprehensive guide, you’ll be well-equipped to determine your Windows version and keep your system running smoothly. Stay informed, and enjoy a seamless computing experience!
#Check Windows version#How to find Windows version#Windows system information#Windows version check#Identify Windows version#Which Windows do I have#Find Windows build number#Windows edition info#Determine Windows version#Verify Windows version#Windows settings check#System info Windows#Windows version tutorial#Windows version guide#Command prompt Windows version#Run dialog Windows version#Windows specifications#Windows version number#Latest Windows version#Windows upgrade info
0 notes
Text
Node.js for the win
For the Bible Project (see earlier posts), switching to a Public Domain version wasn't that difficult on the JavaScript side of things. Server-side, taking the data and writing it to a file was very easy with Node.js, Express.js, and Node's file namespace (specifically writeFileSync()).
Client-side, the JavaScript was rather simple, and having DOM-parsed a number of kinds of Bible-related web pages over the past few weeks, redoing my work came naturally, along with some things I wish I had done, such as checking whether the verses I was pulling were proceeding 1-by-1 with no skips or misses. If the DOM-parser found a missing verse or verses, it would use prompt() to ask if I wanted to continue processing (and the answer was always no, since it usually meant I was missing HTML element CSS classes I needed to parse).
This time, I automated the client-side process fully, waiting just 1 ms between the data having been pushed to the server successfully and me changing the window.location to the next chapter/page for parsing. The entire Bible probably took about 5 to 10 minutes to process, were I to do it all at once. Since I had to stop and change things for skipped verses, I don't know exactly how long it took, just that it was about a page or two each second and 1189 pages / 2 per second = 594.5 seconds, which would be about 10 minutes.
The start of the process, which occurred on page load, also prompted to be sure I wanted to start going page-to-page.
To add the client side JavaScript to the HTML I wanted to scrub, I used PowerShell to append the contents of a file to the bottom of every page representing a Bible chapter (and I found those filtering directory list results by the name of each file).
For the Worldwide English Bible, I also got all the Apocrypha / Deuterocanonical books, but I've skipped those for post parsing, sticking to the 1189 chapters/pages I expect and want to handle first. Still, I do have the JSON for the extra content, which is over 200 pages/chapters.
My text replace list had over 500 entries for the NIV Bible, so I had to translate those into the W.E. Bible. That was a complex project to itself, so I'll detail it in the next post, but suffice to say that I love the flexibility and power of PowerShell to work against CSV and JSON files as objects. The syntactic sugar of that programming CLI made everything I wanted to do rather easy and easy to prototype before going whole hog. For instance, Select-Object -First 2 came in *really* handy to make sure I would get what I wanted for a small subset for each step of translating text replacements from one version to another. The original goal of my project, which was simply to see what the Bible looked like taking the word "Lord" and replacing it with "Earl" happened a while back. It just seems like a cool thing to be able to do just for fun.
0 notes
Text
(2024-02-07) Testing Active Directory Replication Latency/Convergence Through PowerShell (Update 5)
A new version of the AD Replication Convergence Check script has been published containing updates, improvements, and bug fixes. Read more about it, and get the new version of the script, by clicking HERE. Any feedback, or feature requests? Just let me know! Oh, and I almost forgot to mention it, make sure to read the documentation first and also try it out first in a TEST environment to see how…

View On WordPress
0 notes
Photo

How to check the Powershell version ? Powershell version can be easily checked by using the following command in the powershell $PSVersionTable
0 notes
Text

Do you wanna join me (@scoobydoodean) in trying to make gifs of the highest quality possible using only free tools, with workflows as painless as possible??? Here you can find gif-making tutorials, software tests, and comparison and example sets of gifs made using free tools!
Navigation
Very very basic "How a Gif Works"
Best Practices for Quality/Best Visual Result When Uploading Gifs to Tumblr (regardless of gif-making method)
How To Reduce The File Size of A Gif
Sourcing Video Files
Full tool list on Google Sheets with filters

TUTORIAL 1 | RECOLORED GIFS
Making GIFs with DaVinci Resolve and FFmpeg or Gifski
LINK | EXAMPLE SETS
This is how I usually make my gifs. I find it to be the most efficient and most versatile (in terms of coloring, captioning, clipping) of all the methods I've tried for making quality gif sets. This method also does not require the traditional process of screencapping a scene frame by frame which to me is a huge bonus.
Operating systems: Mac, Windows, and Linux. DaVinci Resolve is a pretty high power software though and it does have hardware minimum requirements.
Needed software: DaVinci Resolve and either FFmpeg or Gifski (GUI or CLI version).
Difficulty: Moderate
Time: 🐢🐢 _ _ _ (example set took me 17 minutes)
Input: video files
Competencies: Some general familiarity with video editors and using your computer's shell helps but isn't required. Mac and Windows users: There is a workaround that allows you to avoid the command line. Familiarity with recoloring tools is great but not required.

TUTORIAL 2 | NON-RECOLORED GIFS
Giphy Capture and Gifski
LINK | EXAMPLE SETS
If you are on Mac and just getting into Gif-Making, this is a great way to learn the ropes with what is probably the most intuitive gif-making tool I have ever used. I would just recommend giffing scenes that take place outdoors or in well-lit rooms since you can't make color adjustments.
Operating systems: Mac
Needed software: Giphy Capture and Gifski (GUI version)
Quality potential: High for non-recolored sets! Watch out for odd frame rate effects.
Difficulty: Easy AF
Time: 🐢 _ _ _ _
Input: Any video you can play on your screen that doesn't have screencapture protections in place.
Competencies: None. Very very beginner friendly.
TUTORIAL 3 | RECOLORED GIFS
Pure FFmpeg: Making GIFs with Command Line Scripts
LINK | EXAMPLE SETS
If you love command lines, this one might be fun to you—and YES—you do get visuals. Command line haters: check out Tutorial 4 for a similar process but in a GUI tool.
Operating systems: Mac, Windows, and Linux
Software needed: FFmpeg
Difficulty: Advanced as far as gif-making, but this is actually a good first shell scripting project in my opinion if you've ever wanted to learn how. (I learned a lot about how my command line works while making this tutorial!) For people familiar with bash scripts, I think this will probably be easy!
Time: 🐢🐢🐢🐢🐢
Input: Video files OR frame by frame screencaps if you have them already.
Competencies: General familiarity with your computer's shell (Powershell on Windows, Terminal on Mac) helps a lot! I will try to make it as easy as possible to follow.
NOTE (for Command Line Aficionados): If you are interested in expanding on/improving this tutorial, or making a video -> GIFs version instead of videos -> frames -> GIFs, this is very possible to do. There is also a wealth of troubleshooting help and community-based example scripts for FFmpeg available online through r/FFMPEG and Stack Exchange, and almost all visual filter and complex filter options can be used on any input/output combination in FFmpeg.

TUTORIAL 4 | RECOLORED GIFS
Making Gifs for Free With PhotoScape X
LINK | EXAMPLE SETS
I really like this method as far as the quality you can achieve, and it's pretty easy to use. I plan to try to make more sets with this method later.
Operating systems: Mac and Windows
Quality potential: High
Software needed: PhotoScape X; a frame by frame screencapoing method (See FRAME BY FRAME SCREENCAPPING METHODS/TOOLS section below for a list of methods for this that I've catalogued).
Difficulty: Moderate.
Time: 🐢🐢🐢 _ _
Input: Frame by frame screencaps.
Competencies: General familiarity with photo editors helps but is not required to follow this tutorial.

TUTORIAL 5 | RECOLORED GIFS
Making Quality Gifs For Free On iOS and Android
LINK
If you don't have a computer, just an Android or iOS device, you can still make GIFs! This ones for you!
Operating systems: iOS and Android
Software needed: VITA and a video-to-gif utility or app (ezgif.com or Better Gif Maker shortcut (iOS only))
Time: 🐢🐢 _ _ _
Input: Video files
Difficulty: Moderate.
Requirements: General familiarity with photo editors helps but is not required to follow this tutorial.

EXTERNAL TUTORIAL 1 | NON-RECOLORED GIFS
u/ChemicalOle's "GIMP Gifs 101"
LINK | EXAMPLE SETS
This tutorial is 8 years old. See External Tutorial 2 for a newer tutorial or see NOTE 1 below.
Operating systems: Mac*, Windows, and Linux
Needed software: GIMP with AnimStack; FFmpeg; VLC Media Player
Quality potential: Untested (tutorial needs to be updated)
Difficulty: Untested (largely—I haven't tested captioning with AnimStack yet)
Time: 🐢🐢🐢 _ _
Input: Frame by frame screencaps.
Competencies: Some general familiarity with GIMP and your computer's shell helps but isn't required to follow the tutorial.
LIMITATIONS: 1) Frame by Frame gif-making methods can take up a lot of space on your drive in the interim. 2) A community-contributed GIMP plugin called AnimStack is required. Plugins could break after a GIMP update or developers could simply abandon them at any time.
____
NOTE 1: If you want to try this tutorial, note that 1) There is no longer any need to install GAP separately. It is now part of your regular GIMP install. 2) Filters > Animation > Optimize (for GIF) can be used in place of the color index step. 3) *Author states the tutorial is Linux and Windows, but I see no reason here in 2023 that you can't also follow this tutorial on Mac.
NOTE 2, for Mac users: You may not have to do this, but I had to manually create the scripts folder on Mac to place animstack.scm there. If you need to make the scripts folder, you should place it within the Library/Application Support/GIMP/2.10 folder.

EXTERNAL TUTORIAL 2 | RECOLORED GIFS
DekaythePunk's "How to Make Gifs On GIMP"
LINK
Dekaythepunk has made many tutorials on using GIMP to make gifs and graphics using special coloring techniques and edits. You can find all of their tutorials here.
Operating systems: Windows, Mac*, and Linux.
Needed software: GIMP with AnimStack, G'MIC-QT or McGIMP*, and Layers Effects plugins; a way to screencap frame by frame.
Difficulty: Untested (I'm working on it :D).
Time: 🐢🐢🐢 _ _
Input: Frame by frame screencaps.
Competencies: Some general familiarity with GIMP is helpful but isn't required to follow the tutorial.
LIMITATIONS: 1) Frame by frame gif-making methods can take up a lot of space on your drive in the interim. 2) Community-contributed GIMP plugins are required. These plugins could break after a GIMP update or developers could simply abandon them at any time. (Mac users: also see NOTE 1).
*NOTES (for Mac users):
A G'MIC-QT installer is no longer officially supported for Mac by the makers of the plugin. However, you should be able to install McGIMP on Mac which includes G'MIC, and will also find and use your AnimStack scripts from regular GIMP (McGIMP page | Homebrew install).
You may not have to do this, but I had to manually create the scripts folder on Mac to place animstack.scm there. If you need to make the scripts folder, you place it within the Library/Application Support/GIMP/2.10 folder.
I installed GIMP, then added my AnimStack scripts to GIMP and ensured they worked, then installed XQuartz, then installed McGIMP via Homebrew (you can also just use the provided installer).

EXTERNAL TUTORIAL 3 | RECOLORED GIFS
Lacebird's "How to Make A GIF With Photopea"
LINK
Theoretically, you should be able to use this tutorial to make nice GIFs even on a Chromebook.
Operating systems: Any. Photopea is a browser-based GUI. However, if your device has a very small amount of RAM or you are using certain browsers, you may have issues with the page reloading. You may also need to test with different browsers to see which internet browser manages your available RAM best (I used Brave to test this tutorial out).
Needed software: A good internet browser; whatever software you use to screencap. (See FRAME BY FRAME SCREENCAPPING METHODS/TOOLS section below for a list of frame by frame screencapping methods I've catalogued).
Difficulty: Moderate.
Time: 🐢🐢🐢 _ _
Input: Frame by frame screencaps.
Competencies: Helps to have some familiarity with photo editors or drawing softwares with layer panes.
LIMITATIONS: 1) Frame by frame gif-making methods can take up a lot of space on your drive in the interim. 2) You need a good internet connection to run this smoothly. 3) If your computer doesn't have a lot of RAM or you use certain internet browsers, you may have issues with the page reloading. You can backup your project as a PSD repeatedly in the event of a page reload.

VIDEO/GIF -> OPTIMIZED GIF TOOLS
These are tools that receive a video input or a large GIF and output an optimized/compressed GIF for the web.

FFMPEG
The linked scripts below receive video clips you've already cut to length and captioned (for example, in DaVinci Resolve—see Tutorial 1) and render them into optimized GIFs.
SCRIPT 1 TUTORIAL | SCRIPT 2 TUTORIAL
Interface type: Command Line (CLI).
Difficulty: Moderate.
Operating Systems: Mac, Windows, and Linux.
Input: Video files.
GIFSKI
Gifski was made purely for compressing videos into quality, optimized GIFs and absolutely nothing else. It is meant to be combined with other tools and it is very, VERY good at what it does.
GUI AND CLI SCRIPT TUTORIAL
Interface type: Graphic User (GUI) and Command Line (CLI).
Difficulty: Easy (GUI); Moderate (CLI).
Operating Systems: Mac, Windows, and Linux (CLI only).
Input: Video files (MP4).
EZGIF.COM OPTIMIZE PANE
The Ezgif Optimize tab will receive video files, existing GIFs, or a collection of image files to render into a GIF, and optimize them for upload in other tools.
Interface type: Web-based GUI.
Difficulty: Easy to Moderate.
Operating Systems: Any. You just need a web browser.
Input: Image files (GIF, JPG, PNG, APNG, HEIC, MNG, FLIF, AVIF, WebP) or Videos files (MP4, WebM, AVI, MPEG, FLV, MOV, 3GP).

FRAME BY FRAME SCREENCAPPING METHODS/TOOLS
You can get screencaps of videos frame by frame in several different media players, with various levels of clunkiness/tediousness. I am cataloguing various methods in this section. If there is a method you use and like that is not listed here, please let me know.

FFMPEG
This is my preferred method for grabbing caps. If you aren't scared of the idea of opening your command line, this is absolutely the most efficient and versatile way to get source-resolution quality frame by frame screencaps.
TOOL TUTORIAL 4
Operating Systems: Mac, Windows, and Linux
Interface type: Command Line (CLI).
Difficulty: Even if it's your first ever script, I think you can do it! I have a template for you and an example in the linked tutorial and I believe in you! :D
Input: Video files of any extension.
SCREENTOGIF
If you're on Windows, this is a nice, intuitive way to get frame by frame caps. However, note that the resolution of your caps will be limited by the resolution of your computer screen.
Operating Systems: Windows
Interface type: Graphic User (GUI)
Difficulty: Easy (for batch capping)
Input: Any video you can open and screencapture.
VLC MEDIA PLAYER
VLC has a function that can automate frame by frame screencapping, but to be honest, I have had difficulties getting it to work properly. However, you can also screencap manually frame by frame in VLC with hot keys.
EXTERNAL TUTORIAL
Operating Systems: Windows, Mac, and many popular Linux distros (Debian, Ubuntu, Mint, ArchLinux, and more).
Interface type: Graphic User (GUI)
Difficulty: Easy (for batch capping)
Input: Any video you can open and screencapture.
NOTE for mac users: If you want to try the automated method, there is no section called "Preferences" in the Mac app. To reach the proper menus, in the top menu in VLC, click "VLC Media Player" > Settings > Video, then click the Show All button in the bottom left corner.
EZGIF.COM
Ezgif.com is a web-based GUI, so it can only accept a video file so large and is limited to a 20 FPS capture for 10 seconds at a time. However, if you have short clips or maybe a Youtube video you've downloaded, this is a good option.
TOOL TUTORIAL 5
Interface type: Web-Based Graphic User Interface (GUI)
Difficulty: Easy.
Operating Systems: Any. This is a free online tool.
Input: Any video clip under 100 MB. If you have a whole episode of TV, you'll have to clip to just the scene you want first to make your video file small enough to upload.


This section is for partial tutorials with one or more hurdles to being posted as a full tutorial (ex: not able to crop, not able to apply the same action to multiple frames at a time with ease, etc). If you want to pick up where I left off to troubleshoot/come up with workarounds (or maybe use the utilities that are available in a given tool to cover gaps in others) you're welcome to give it a whirl—and let me know if you make any headway!

UNFINISHED WORKFLOW 1 | LINK
Making GIFS with Autodesk Sketchbook
Operating systems: Mac and Windows
Needed software: Autodesk Sketchbook
Quality potential: High for non-recolored sets, but has various limitations to implementing coloring (even though some coloring options are supported) and also cropping.
Difficulty: Easy
Competencies: None.
ISSUES:
Can't crop frames in Flipbooks (you could crop externally with FFmpeg, GIMP, ezgif.com, Photoscape X).
Native text captioning options don't support outlining your text and have very limited drop shadow settings.
Limited FPS export options.
If you wanted to recolor your set, you'd have to do it one frame at a time in a very tedious way.


Let me know of any tools you think I should look into that aren't on this list!
✅ Tools I have tried + shared at least one tutorial.
🔄 Tools I am in the process of testing or have finished testing but have not shared a tutorial for yet.
☑️ Tools I am aware of but haven't tested yet.

GRAPHIC USER INTERFACE (GUI) TOOLS
DOWNLOADABLES
✅ DaVinci Resolve
✅ Gifski
✅ Giphy Capture
🔄 ScreenToGif | No tutorials yet
✅ Photoscape X
🔄 GIMP | WIP Testing | External tutorials available
✅ Autodesk Sketchbook | Unfinished Workflow
☑️ Blender
BROWSER-BASED
✅ Photopea.com
✅ Ezgif.com
COMMAND LINE (CLI) TOOLS
✅ FFmpeg
✅ Gifski
☑️ Image Magick
☑️ Gifsicle
40 notes
·
View notes
Text
How to Optimize Windows 10 for Gaming and Performance!!!
Windows 10 is doing exceptionally well in every area. It is magnificent while working on various applications. Windows 10 is also the notch choice of gamers as it allows them to feel the zest of the game completely. The strong OS Windows 10 provides the required configuration and speed to suppose all the popular and heavy games. Here in this article, we will share with you certain ways by which you can optimize your Windows 10 for gaming and higher performance.
Optimize Windows 10 With Gaming Mode
Windows 10 has gone through several updates, and each update brings something new. The latest release of Windows 10 was a gift for gamers as it brought gaming mode optimization. To optimize Windows 10 with gaming mode, follow the below steps:
Initially, after turning your System on, you have to press the Windows key + I
This will redirect you to the Settings panel of your System. There in the search bar type game mode
Out of two options, Click Game Mode settings or Turn on Game Mode; you have to click anyone.
A screen will appear in front of you with the name ‘game mode.’
You have to switch the button of game mode to on from off to optimize it.
And here your PC is ready to function in your gaming mode.
Disable Nagle’s Algorithm to Enhance Gaming
Nagle algorithm might be the friend of your System, but it is an enemy of gaming in PC. While Nagle’s algorithm is enabled in your PC, it is going to temper your gaming speed. So it will be better if you turn off Nagle’s algorithm settings of your PC. to disable it follow the below steps:
Press Windows key + X
Out of all the other options you have to select Windows Power Shell
After that, on the appeared screen you have to Enter ipconfig
Then search for “IPv4 address” to know your PC’s IP address
Once you know your IP address, edit the Windows Registry:
To register first Click Start
Then search by Typing Regedit
Further, Select Registry Editor
Once the registry editor is opened, you have to copy and paste the following path in the address bar:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces
After this step, you will find a list of folders in the left-hand pane. Every folder will have file names mixed up of letters and numbers. You have to match your IP address with t DhcpIPAddress to locate the correct file. After that follow the below steps;
Right-click on the folder
Then Select New > DWORD (32-bit) Value
You have to Name this as TcpAckFrequency
Then click on the OK button.
After that Select New > DWORD (32-bit) Value again
Again Name this one TCPNoDelay.
Double-click on each and set their parameters to 1
Complete these steps and you are done disabling Nagle’s Algorithm.
Make Online Gaming improved With Faster DNS.
Optimizing Windows 10 online gaming with faster DNS will improve your online gaming experience. It avoids network traffic as it contains faster internet. To make your online gaming fun follow the below steps;
Once you have turned your system on, you have to press Windows + I which will redirect you to the Settings page.
On the settings page you have to look for Network and Internet > Change Adapter Settings.
Then Right-click on your wireless network
Further, you have to Select Properties
And then Highlight Internet Protocol Version 4.
Later on, you have to make a note of the two DNS entries
Then replace them with 1.1.1.1 and 1.0.0.1.
After you are done with this press OK and restart your default browser.
After you finish the last step, your online gaming is going to be super fast and fun.
Turn off automatic updates.
As mentioned above, Windows 10 keeps renewing itself with several updates. The updates are to make the functioning of your System better, but it might create a hindrance for your gaming task. To ensure fast gaming, you have to disable automatic updates for better Windows 10 gaming, and to do that follow the given steps:
First of all open Open Settings either from the start button or with the Windows key + I
Then Click Update and Security and select Windows Update
There you have to search for Advanced options and after that click Update Options
You have to disable auto-updates.
Then Enable Show notification as it will hint you about every update your System is going to get
And then you are done improving your gaming quality.
Disable Notifications in Windows 10 to avoid Gaming Hindrance
Many times you have turned on notifications so that you do not miss anything important. But these notifications popping create a hindrance for your gaming.
You have to turn off pop-ups to enjoy better gaming. Follow the below steps to disable notifications in Windows 10:
First of all open settings by searching it on the start button or hitting Windows + I
Then click System and select Focus Assist
Further, you have to Select Alarms Only as it will hide all other notifications except important alarms and reminders.
And you are done disabling notification on your System which will promote faster gaming.
Prevent Steam Auto-Updating Games
People who play games on windows generally install it from steam. many a time its auto-update feature might drink up all your internet and speed resulting in lower gaming. It is better to shut its update feature off and enjoy a high gaming experience:
Initially, you have to launch the Steam client that will boost your gaming.
Then open Steam and look for Settings. There open Downloads
Lastly uncheck Allow downloads during gameplay
Windows 10 Visual Effects Needs to be altered
Graphical User Interfaces (GUI) of your System might be creating a hindrance to your gaming speed by affecting the processing speed.
Alter the settings of visual effects for better game improvements.
First, you should open Settings with Windows key + I
Then type “performance.”
You should then select Adjust the appearance and performance of Windows.
Then in the settings box, select Adjust for best performance
Click on Apply
Then click the Advanced tab
Make sure that Adjust the best performance of his set to Programs
Then click on Apply again, then OK to confirm
Alter Your Mouse Settings for better Windows 10 Gaming
It might shock you, but a little tweak in your mouse settings can create a huge impact on the overall performance of your System. When it comes to PC gaming tweak your mouse settings to optimize your Windows 10 for gaming in a better way:
Firstly, open Settings
Then click Devices and then open Mouse
Click on view to see the Pointer Options tab
Then clear the Enhance pointer precision checkmark
Then Click Apply
Lastly, click OK to exit—you can also adjust the pointer speed to suit
Power Plan Enhances your gaming experience
Alter your power settings to find out its effect on your PC. You need to follow the following steps to maximize your power plan:
First of all, you should open Settings
Type in ‘power’.
Then click Power & sleep settings and open Additional power settings
Then select the high-performance option
If it is not available, use the Create a power plan to configure a new, custom power plan
This option allows your PC to perform better at the cost of higher energy consumption and temperature levels. For this reason, it is better to have an activated Windows 10 optimization on the desktop rather than laptop PCs.
Install DirectX 12 to Optimize for Gaming
DirectX 12, is the food for faster online gaming. It enhances the support system of gaming that is CPU and GPU.
Follow the below steps To check if you have the latest version of DirectX:
First, you should open Windows PowerShell
Then type dxdiag
After that tap Enter
Soon, you will be able to see the DirectX Diagnostic Tool.
To fix the issue of non installed DirectX follow these steps:
First, you should open Settings with Windows key + I
Then select Update and security
Open Windows Update and there you have to click on Check for updates
Wait for the updates to install
Many gaming settings will be automatically optimized by DirectX12 in Windows 10.
This is all you need to do to optimize faster gaming in your System. If we missed something, let us know in the comment box.
Thanks for reading this
To your Success,
Aman Yadav
2 notes
·
View notes
Text

The one thing about cyber security that you should always be aware of is its ongoing state of evolution. Threats are constantly evolving; thus, your defensive strategy cannot become inert. This is not overly dramatic. Attacks occurred around every 39 seconds in 2023. Approximately 40% of all attacks are script-based, meaning that malevolent actors have unlimited access to resources. IT experts and managed service providers (MSPs) and rmm tools and PSA software suppliers must exercise caution. We have compiled a list of some of the biggest cybersecurity threats and vulnerabilities from recent history to assist. This is the impact of the shifting landscape on security-conscious individuals. What is cyber security? A catch-all word for reducing the risks of cyberattacks is cybersecurity. Organizations employ a range of procedures, technologies, and controls to practice adequate cyber security, including: Keep information, software, hardware, networks, and other assets safe from real-time unauthorized access and exploitation. Examine potential risks Practice emergency response and simulate hacking. reaction techniques Establish policies to encourage the safe use of information and technology. How do vulnerabilities and threats to computer security operate? Malicious actors can obtain unauthorized access to sensitive data through many means. Also Read: What is SHA256 Encryption: How it Works and Applications Existing weaknesses are often exploited in events. For example, hackers may leverage a widely recognized vulnerability to obtain backdoor access. Alternatively, they can uncover fresh vulnerabilities associated with your technology usage. In either case, these incidents frequently involve ransom demands, legal dangers, and bad public relations. Not every bad actor is a Hollywood hacker working for a hidden organization of cybercriminals. Anyone can cause a breach, even a contracting agency, from irate workers and roguish states to terrorists and corporate spittle. Strong safeguards should be put in place before that occurs! Here are a few of the most noteworthy threats that have emerged in the most recent headlines: Twitter Email Leak The Twitter data breach occurred only a few days after the year 2022 came to an end. In summary, the email addresses of more than 200 million Twitter users were exposed on underground hacking websites. The affected Twitter accounts surpassed 400 million. Hackers began gathering data in 2021 by taking advantage of a vulnerability in the Twitter API. Several hackers took use of this vulnerability back in 2021, which led to multiple ransomware attempts and leaks in 2022. One of the biggest data breaches in history is this one. Also Read: Guide to Check Which Powershell Version You are UsingGuide to Check Which Powershell Version You are Using The Royal Mail Hack The UK's Royal Mail was compromised by the Russian ransomware group LockBit in January 2023. The hackers demanded a ransom of £65 million to unlock the compromised data. The business requested that customers cease sending items overseas due to the severity of the event! This may seem like a success story in certain ways. Ultimately, Royal Mail declined to provide a ransom. Unfortunately, there were prolonged service outages and many of its employees had their data disclosed. This cybersecurity event demonstrates that averting a hack's worst-case scenario is a minor comfort. The worst-case scenario persists, and the erosion of public trust is a severe blow for national infrastructure-level companies such as the Royal Mail. The Reddit Hack The forum site Reddit disclosed in February 2023 that the user was a recent victim of spear phishing. Through a phishing attack targeted at employees, hackers were able to access internal Reddit data. In addition, the hackers desired ransom money. THE OUTCOME? Financial information was leaked along with the personal information of hundreds of current and former faculty members, staff members, and advertisers. Reddit's emergency response team was able to resolve the issue swiftly. However, this was an event that the business ought to have completely avoided. The phishing attack functioned by impersonating a page from the internal portal of the business. This tricked at least one worker into disclosing their access credentials—and all it takes is one! T-Mobile Data Breach: T-Mobile USA had two hacks. Late in 2022, T-Mobile disclosed that 37 million users' personal data had been accessed by a malevolent attacker. The most recent breach was found in March. Comparing the volume of stolen data to the previous breach, it was less. A total of 836 customers had their PINs, account information, and personal details compromised due to this cyber security threat. Information on personal bank accounts was not taken. Also Read: What is BSSID? The ChatGPT Payment Exposure The widely used ChatGPT Plus service experienced a major outage in March 2023. Even though the interruption was brief—about nine hours—it caused no appreciable harm. The payment information of more than one percent of subscribers was disclosed to other users. The communication histories of certain users also become accessible. While 1. 2 may not seem like a big number, it represents yet another instance of a lost user's trust. In this instance, OpenAI was unable to properly retrieve an open-source library, a huge mistake! When you are unable to secure your software supply chain, it does not look good. This event might hurt a tech company's competitiveness in an expanding industry like artificial intelligence. Also Read: How To Take Screenshots on Windows and Mac AT&T 3rd Party Data Breach In March 2023, a third-party data breach exposed 9 million customer records belonging to another titan in the telecom industry, AT&T. AT&T classified this threat as a supply chain assault involving data that was several years old and largely related to eligibility for device upgrades. Consequently, the telecom advised its clients to implement more robust password security protocols. VMware ESXi Ransomware In January of last year, a ransomware attack using an outdated vulnerability (CVE-2021-21974) affected about 3,200 unpatched VMware ESXi servers. Via CVE-2021-21974, hackers began a ransomware assault against VMware ESXi hypervisors. They were able to use this readily exploitable vulnerability to remotely exploit code without the need for previous authentication. France was the most affected nation, with the United States, Germany, and Canada following suit. Concerning CrowdStrike, the issue is becoming more serious. "A growing number of threat actors are realizing that an environment rich in targets is created by inadequate network segmentation of ESXi intrusions, a lack of security tools, and ITW vulnerabilities for ESXi." How can MSPs get ready for threats and vulnerabilities related to cyber security? Use these four practical suggestions to enhance your cybersecurity strategy and mitigate threats and vulnerabilities: Make data backups a regular part of your life. Adhere to the 3-2-1 backup policy. Store three duplicates of your information on two or more media types. One copy will be stored on your primary system. The other two ought to be locally and cloud-based encrypted backups. Reduce your exposure to the least amount possible. Installing firewalls or antivirus software alone won't cut it. Additionally, you must keep them updated. Also Read: What is a VLAN (Virtual LAN)? Author Bio Fazal Hussain is a digital marketer working in the field since 2015. He has worked in different niches of digital marketing, be it SEO, social media marketing, email marketing, PPC, or content marketing. He loves writing about industry trends in technology and entrepreneurship, evaluating them from the different perspectives of industry leaders in the niches. In his leisure time, he loves to hang out with friends, watch movies, and explore new places. Read the full article
0 notes
Text
Pip Install Mac Terminal

Package Version - - gurobipy 9.1.0 pip 20.2.1 setuptools 49.2.1 Our pip package includes a limited license that allows you to solve small optimization problems. If are an academic user, you can obtain a free, unlimited academic license from our website. Pip install packagename. Pip will look for that package on PyPI and if found, it will download and install the package on your local system. Download and Install pip: pip can be downloaded and installed using the terminal in Linux by going through the following command.
PIL is an abbreviation of Python Imaging Library and it adds image processing to Python. In 2011, PIL has been discontinued—its unofficial successor framework Pillow for image processing is an actively maintained and user-friendly alternative for Python 3.
Let’s dive into the installation guides for the different operating systems and environments!
How to Install Pillow on Windows?
To install the updated Pillow framework on your Windows machine, run the following code in your command line or Powershell:
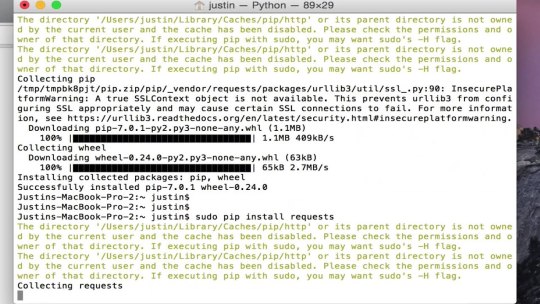
How to Install Pillow on Mac?
Open Terminal (Applications/Terminal) and run:
xcode-select -install (You will be prompted to install the Xcode Command Line Tools)
sudo easy_install pip
sudo pip install pillow
pip install pillow
As an alternative, you can also run the following two commands to update pip and install the Pillow library:
How to Install Pillow on Linux?
Upgrade pip and install the Pillow library using the following two commands, one after the other:
How to Install Pillow on Ubuntu?
Upgrade pip and install the Pillow library using the following two commands, one after the other:
How to Install Pillow in PyCharm?
The simplest way to install Pillow in PyCharm is to open the terminal tab and run the following command:
Here’s a screenshot with the two steps:
Open Terminal tab in Pycharm
Run pip install Pillow in the terminal to install Pillow in a virtual environment.
Install Pip Terminal Mac Os X
As an alternative, you can also search for Pillow in the package manager. However, this is usually an inferior way to install packages because it involves more steps.
How to Install Pillow in Anaconda?
You can install the Pillow package with Conda using the following command in your shell:
This assumes you’ve already installed conda on your computer. If you haven’t check out the installation steps on the official page.
Where to Go From Here?
Enough theory, let’s get some practice!
To become successful in coding, you need to get out there and solve real problems for real people. That’s how you can become a six-figure earner easily. And that’s how you polish the skills you really need in practice. After all, what’s the use of learning theory that nobody ever needs?
Practice projects is how you sharpen your saw in coding!
Do you want to become a code master by focusing on practical code projects that actually earn you money and solve problems for people?
Then become a Python freelance developer! It’s the best way of approaching the task of improving your Python skills—even if you are a complete beginner.
Join my free webinar “How to Build Your High-Income Skill Python” and watch how I grew my coding business online and how you can, too—from the comfort of your own home.
While working as a researcher in distributed systems, Dr. Christian Mayer found his love for teaching computer science students.

To help students reach higher levels of Python success, he founded the programming education website Finxter.com. He’s author of the popular programming book Python One-Liners (NoStarch 2020), coauthor of the Coffee Break Python series of self-published books, computer science enthusiast, freelancer, and owner of one of the top 10 largest Python blogs worldwide.
His passions are writing, reading, and coding. But his greatest passion is to serve aspiring coders through Finxter and help them to boost their skills. You can join his free email academy here.
Using pip to install gurobipy
Most Python installations come with the Python package managementsystem “pip”. You can use pip to download and installthe gurobipy extension simply by opening a terminal window andissuing the following command:
python -m pip install -i https://pypi.gurobi.com gurobipy
This command instructs the called Python interpreter to downloadgurobipy from our private PyPI server(https://pypi.gurobi.com)and install it into your Python environment. Note that ourgurobipy installation package is self-contained, so you can useit without any other software installation steps.
Pip Install Mac Terminal Software
We plan to eventually move the gurobipy package to the publicPyPI server (https://pypi.org), which will remove the need forthe -i argument.
After the installation succeeds, you should see gurobipyamong the installed packages listed upon typingpython -m pip list. For example:
Mac Terminal Install Pip
Our pip package includes a limited license that allows you to solvesmall optimization problems. If are an academic user, you can obtainafree, unlimited academic license from our website.Otherwise, you can obtain a free evaluation license by [email protected].

1 note
·
View note